
As cyber threats continue to evolve, one attack method has emerged as particularly dangerous for businesses: email hijacking through man-in-the-middle (MITM) attacks. This sophisticated form of cybercrime allows attackers to intercept, monitor, and manipulate business email communications—often leading to devastating financial losses and data breaches. Understanding this threat and how to detect it early is crucial to protecting your organisation.
The Primary Threat: Email Hijacking
In our experience working with businesses, email hijacking represents the most common and dangerous form of MITM attack. Cybercriminals gain control of legitimate email accounts—often belonging to financial institutions, suppliers, or even your own staff—and use this access to monitor communications, intercept sensitive information, and redirect payments.
Here's how a typical email hijacking attack unfolds: an attacker compromises an email account and silently monitors correspondence between your business and a trusted partner, such as a supplier or client. They learn about upcoming invoices, payment schedules, and communication patterns. At a critical moment, they intercept an invoice email, modify the bank account details to their own, and send it along as if nothing happened. By the time the fraud is discovered, your payment has disappeared into an untraceable account.
What makes email hijacking particularly insidious is its subtlety. The attacker positions themselves in the middle of existing, trusted relationships. They don't need to create elaborate phishing schemes or suspicious-looking emails—they're working from inside a legitimate account, making their communications appear entirely authentic.
What Is a Man-in-the-Middle Attack?
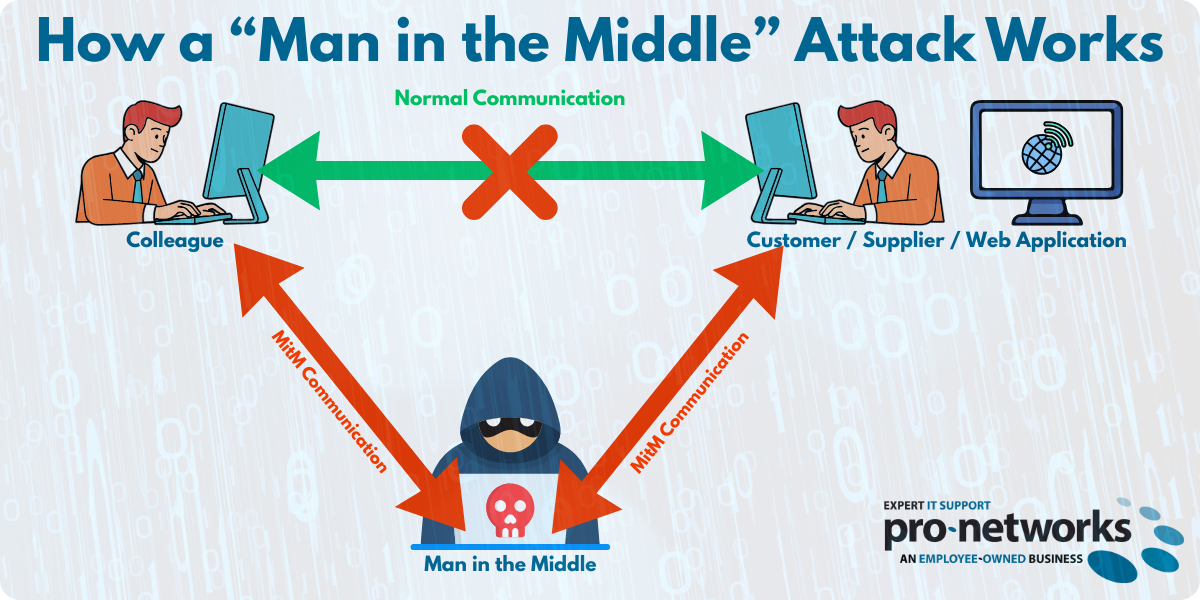
A man-in-the-middle attack occurs when a cybercriminal secretly intercepts and potentially alters communications between two parties who believe they're directly communicating with each other. The attacker essentially creates a scenario where they control the entire conversation without either party realising a third person is present.
When your finance team thinks they're securely corresponding with a supplier about an invoice, they might actually be communicating with an attacker who has compromised that supplier's email account and is manipulating the conversation to redirect payments.
How Do Man-in-the-Middle Attacks Work?
MITM attacks typically unfold in two key phases: interception and decryption.
Interception is where the attacker first gains access to your network traffic. This commonly happens through a compromised email account (please see our blog on how easy MFA can now be breached) or compromised Wi-Fi networks—perhaps that "Free Public Wi-Fi" at a local café or even a malicious access point set up specifically to lure unsuspecting users. Attackers can also use techniques like ARP spoofing to redirect traffic on your local network, or DNS poisoning to send users to fraudulent websites that look identical to legitimate ones.
Decryption follows once the attacker has positioned themselves in the data stream, they can access information that should be protected. They can modify an invoice advising of “updated bank details” – this is unknown to the sender or recipient of the email and is why these attacks are so devastating. Session hijacking is another common tactic, where attackers steal authentication tokens to impersonate legitimate users.
Common Attack Methods
While MITM attacks take various forms, email hijacking stands out as the most prevalent threat we encounter:
- Email Hijacking: The primary threat—criminals compromise email accounts to monitor transactions, intercept invoices, and redirect payments to fraudulent accounts. It is important to remember here that the compromised account may not be at your side of the conversation – your customer or supplier may be compromised
- Rogue Wi-Fi Access Points: Attackers create fake networks with legitimate-sounding names to trick users into connecting
- SSL Stripping: Forcing connections from secure HTTPS to unencrypted HTTP
- DNS Spoofing: Redirecting users from legitimate websites to malicious copies
The Risk to Your Business
Email hijacking poses an immediate and substantial financial risk. Unlike data breaches that may take time to monetise, email hijacking attacks can result in direct financial losses within hours. Businesses can lose tens of thousands of pounds through misdirected payments before they even realise their email communications have been compromised.
Small and medium-sized businesses face particular vulnerability. Research indicates that 43% of all cyberattacks target SMBs, often due to less robust security measures. For companies handling financial transactions via email, the risk is especially acute. A single successful email hijacking attack can result in:
- Direct financial losses from misdirected payments
- Damage to supplier and client relationships
- Regulatory penalties for data breaches
- Reputational harm that impacts future business
- Legal liability if client or partner data is compromised
Protecting Your Organisation
The good news is that effective protection against MITM attacks, particularly email hijacking, is achievable with the right approach:
Implement Identity Threat Detection and Response (ITDR): This is your first line of defence against email hijacking. ITDR solutions continuously monitor for suspicious authentication patterns, unusual access locations, and compromised credentials. By detecting when an email account has been compromised or accessed abnormally, ITDR can alert you to an attack in progress—often before significant damage occurs. This proactive approach is essential for preventing email hijacking attempts that traditional security measures might miss.
Email Security and Authentication Protocols: Implement DMARC, SPF, and DKIM email authentication to prevent email spoofing and verify sender legitimacy. These protocols help ensure that emails claiming to be from your domain are actually from your organisation.
Multi-Factor Authentication (MFA): Require MFA on all email accounts and critical business systems. Even if an attacker obtains login credentials through phishing or other means, they cannot access the account without the second authentication factor.
Employee Training and Verification Procedures: Train staff to recognise warning signs of email compromise, such as unusual payment requests, slight changes in email addresses, or requests to update banking details. Establish verification procedures requiring phone confirmation (using known numbers, not those provided in suspicious emails) for any payment instruction changes.
Monitor for Anomalies: Beyond ITDR, deploy comprehensive network monitoring tools (including a SIEM solution) that can detect unusual activity patterns, such as emails being forwarded to external addresses or large data exports from email accounts.
Taking Action
For businesses of all sizes, protecting against email hijacking isn't optional—it's essential. Man-in-the-middle attacks, particularly those targeting email communications, represent one of the most direct financial threats your organisation faces. However, with proper security measures, especially Identity Threat Detection and Response (ITDR) solutions, employee education, and expert IT support, your organisation can substantially reduce its risk.
If you're concerned about your company's vulnerability to email hijacking or need help implementing ITDR and robust email security measures, professional IT support can make all the difference. From deploying advanced threat detection to establishing verification procedures and conducting staff training, protecting your business requires both technical expertise and ongoing vigilance.
Don't wait until after a compromised payment to take email security seriously. The time to strengthen your defences is now.
Speak to us to find out how we can help you.
