
Every business, regardless of size, is under threat of cyberattack. Thinking you’ll never be a victim because there are bigger and better targets out there is a fallacy and a dangerous stance.
Who is Attacking You?
Cyberattacks happen all day, every day. Attacks against targets like Hilton Hotels, British Airways and Uber may grab the headlines, but attacks of that scale are a tiny portion of cybercrime. They’re carried out by skilled, well-funded, teams who choose targets that will give them a big profit.
The good news is you probably don’t need to worry about that type of attack. The bad news is, it’s the other 99% of attacks that you do need to worry about. The cybercriminals that are coming after the average SME don’t select their targets at all. Their victims nominate themselves by being unprotected, insecure and untrained.
Machine Gunners, Not Snipers
To explain this, we’ll look at some common attack types. Phishing attacks are the most common form of cyberattack.
They’re a low-skilled attack. They use a fraudulent email to make the victim do something that benefits the attacker. Opening an attachment for example, could install malware. Clicking a link might take the victim to a fake web page designed to harvest the victim’s login credentials.
The email recipients haven’t been specifically chosen. Every time there is a major data breach, the leaked data is made available on the dark web. Cybercriminals download it and use it as the ammunition for their automated emailing software.
You can check whether an email address has been exposed in a data breach by entering it on the (safe) website Have I Been Pwned.
If the top-tier hackers are like snipers who carefully select and stalk their targets, the cybercriminals behind phishing campaigns are machine gunners. They randomly spray bullets, then see who they hit.
Vulnerabilities: The Low-Grade Hackers Way In
Even without the skills of the top-tier hackers, the criminally-minded can breach networks by exploiting vulnerabilities in software. Applications and operating systems must be regularly patched and updated to fix bugs and eradicate known vulnerabilities.
But there’s software inside hardware too. Managed switches, routers, firewalls and other network appliances all contain software. If you don’t patch the firmware in your network appliances, their vulnerabilities will never be addressed. And vulnerabilities can be exploited. Think of it as an equation.
A vulnerability + an exploit = a compromised system.
A Case in Point: Log4j
Here’s an example. The Log4j vulnerability hit the headlines in the closing weeks of 2021. Log4j is a software module used the world over by software authors. A vulnerability was discovered in Log4j that allowed a hacker to perform illegal actions like taking control of a vulnerable system or spreading malware.
Specialist websites list the characteristics of known vulnerabilities so that cyber security professionals can research them. The vulnerabilities, known as common vulnerabilities and exposures, are given a unique CVE number.
A quick search finds several vulnerabilities related to Log4j. Here’s the details of one, designated CVE-2021-44228. We’ll search for that number on GitHub, the famous software repository.
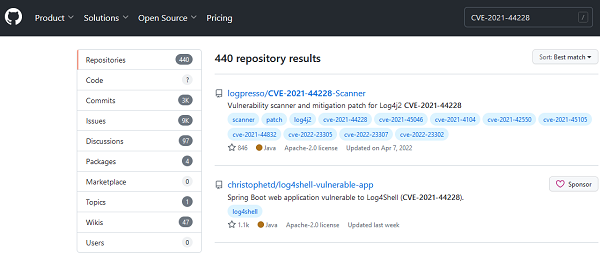
That yields 440 results. All of those results have sample code that you can download, compile and use to exploit that vulnerability. You only need to follow the technical but relatively simple instructions. No hacking skills required.
Another website is a search engine for internet-facing equipment and systems. It can be misused to identify systems affected by any CVE. We’re not linking directly to these sites.
The results can be downloaded and fed into automated attack software, available from the dark web. It probes each system in turn, trying to use the exploit.
So again, you’re not being selected and targeted by a human being. You’re putting yourself in the firing line because of bad cyber hygiene.
How We Can Help?
Plainly, everyone is a target. Regardless of industry or profession, business size or location, if you’re connected to the internet you are at risk of attack.
Our examples are just two of an almost endless list of attack types. Keeping up with the changing cyber landscape, assessing your cyber risk and implementing the appropriate defensive measures is an overwhelming prospect.
A robust cyber posture has three components: technology, governance, and training. Like a three-legged stool, it won’t stand up if one of them is missing or undersized.
Technology refers to the automated, always-on-duty, software and hardware that detects and neutralizes threats. Endpoint security software traps viruses and other malware. Firewalls with built-in gateway security protection can monitor and control the border crossing between your business and the internet. Unauthorized or malicious traffic is stopped dead.
Other technology-based security measures are not automated. Penetration testing probes your network, looking for vulnerabilities. Remediation will then address any vulnerabilities. This has to be repeated periodically because new vulnerabilities are discovered all the time. Internal vulnerability scans serve a similar function, inside your network.
Governance means the controls you have in place to ensure your IT resources are used only in company-sanctioned ways. By controls, we mean policies and procedures, such as a Password Policy or Acceptable Usage policy.
Activities such as patching and penetration testing need to be performed in a regular and timely fashion, with any remediation ranked, prioritized and implemented. Governance will ensure these take place.
Compliance with standards such as GDPR, DPA2018, CyberEssentials and ISO27001 tightens your cyber security and improves your data protection.
Training staff is essential. Staff are being asked to do more and more, from recognizing cyber threats and knowing how to react, to realizing when a subject access request is being made.
They’re on the front line protecting your business. Training is the only way to make them effective.
The Cyber Security Cycle
Cyber security isn’t something you fit and forget. It is a discipline requiring constant review, testing and maintenance.
Pro-Networks can assist with your cyber security technology solutions, the development and roll-out of governance and training of your staff.
Click here to get in touch with us in connection with all of your cyber security needs.
